In the intricate tapestry of software development, where creativity converges with functionality, lies a critical factor that often determines success or failure: security. A record 26,448 software security flaws were reported in 2022, with the number of critical vulnerabilities up 59% in 2021 to 4,135. The cost of cybercrime is predicted to hit $8 trillion in 2023 and will grow to $10.5 trillion by 2025, according to the 2022 Official Cybercrime Report by Cybersecurity Ventures.
At a time when almost all software contains open-source code, at least one known open-source vulnerability was detected in 84% of all commercial and proprietary code bases. These figures serve as a clarion call for a proactive approach to code audits.
This article discusses what is a software code audit, the types of software code reviews, and what’s the price of a software code audit.
Key points
What is a software code audit?
Software code audit is a process of analyzing and reviewing software source code to identify potential problems, bugs, vulnerabilities, and inconsistencies with programming standards and best practices. This process is performed to improve the quality and security of a software product.
Internal specialists, external security experts, or specialized companies can perform software code audits as well as other services. The code audit is often necessary to choose a proper digital transformation platform and eliminate possible problems in future.
Why is code auditing necessary?
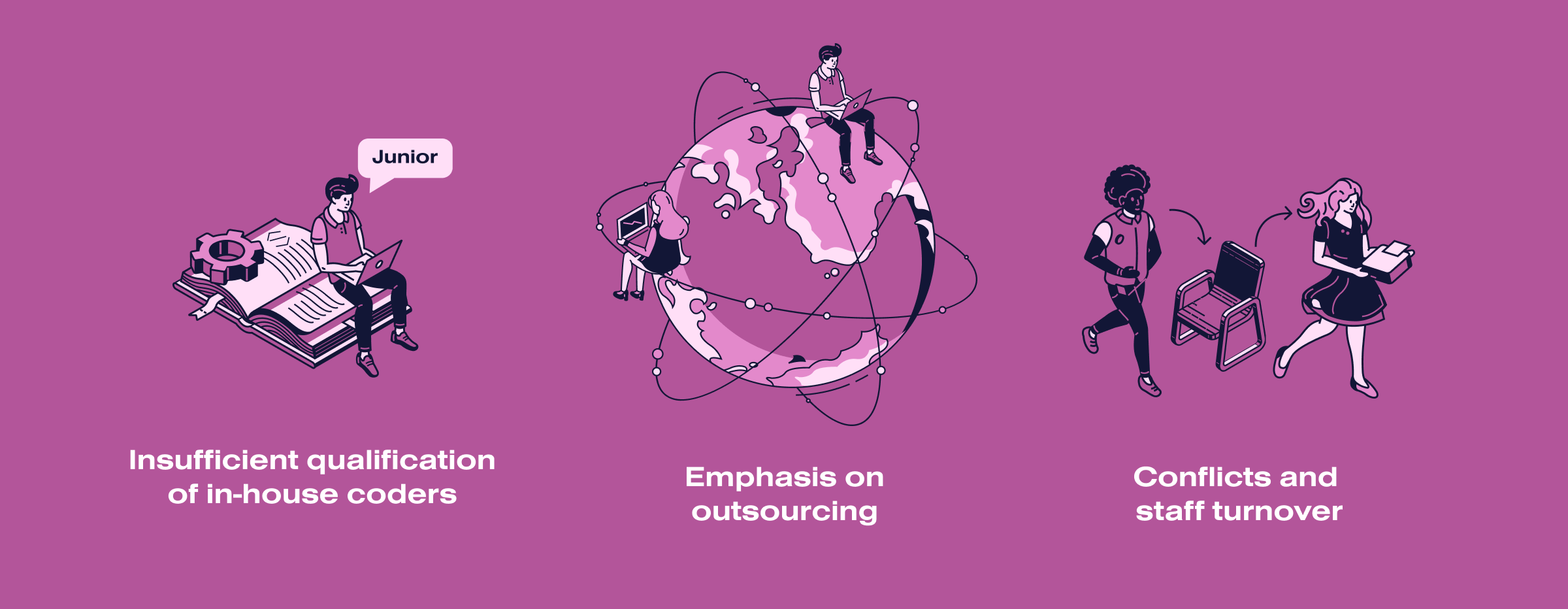
Many IT companies think that attackers simply don’t care about them. However, worldwide experience proves otherwise. Even niche and unpopular applications often become the object of planned hacker attacks. And as a consequence, serious losses for the development company: financial and reputational. The prerequisites for trouble due to cyberattacks are mainly:
- Insufficient qualification of in-house coders. Junior developers often work as Middle developers, and as soon as they grow up to the required level, they immediately get Senior responsibilities. But these titles are not just an indicator of status and salary. They characterize a complex understanding of the development process, including information security. Such a mismatch can result in errors in designing critical software subsystems.
- Emphasis on outsourcing. Businesses cannot do without contractors. However, not all are equally competent and decent. As a result, source codes and information about software architecture become known to many people. There is no guarantee that none of them are related to the hackers.
- Conflicts and staff turnover. The authors of code threats are often not spies but ordinary employees convinced they have been mistreated. The consequences of such revenge can be devastating. That is why increasing staff loyalty and strengthening corporate spirit are not empty words but some of the aspects of code security.
So, a periodic software code review is necessary no matter what team you have.
What are the dangers of unintentional software code vulnerabilities?
Introducing logic bombs, undocumented destructive functions, master passwords, or, for example, obviously incorrect encryption algorithm implementation demands time and resources. And the more complex and expensive the hack is, the fewer attackers will follow through with the operation. Common coding incorrectnesses are another matter. Even casual hackers can take advantage of them.
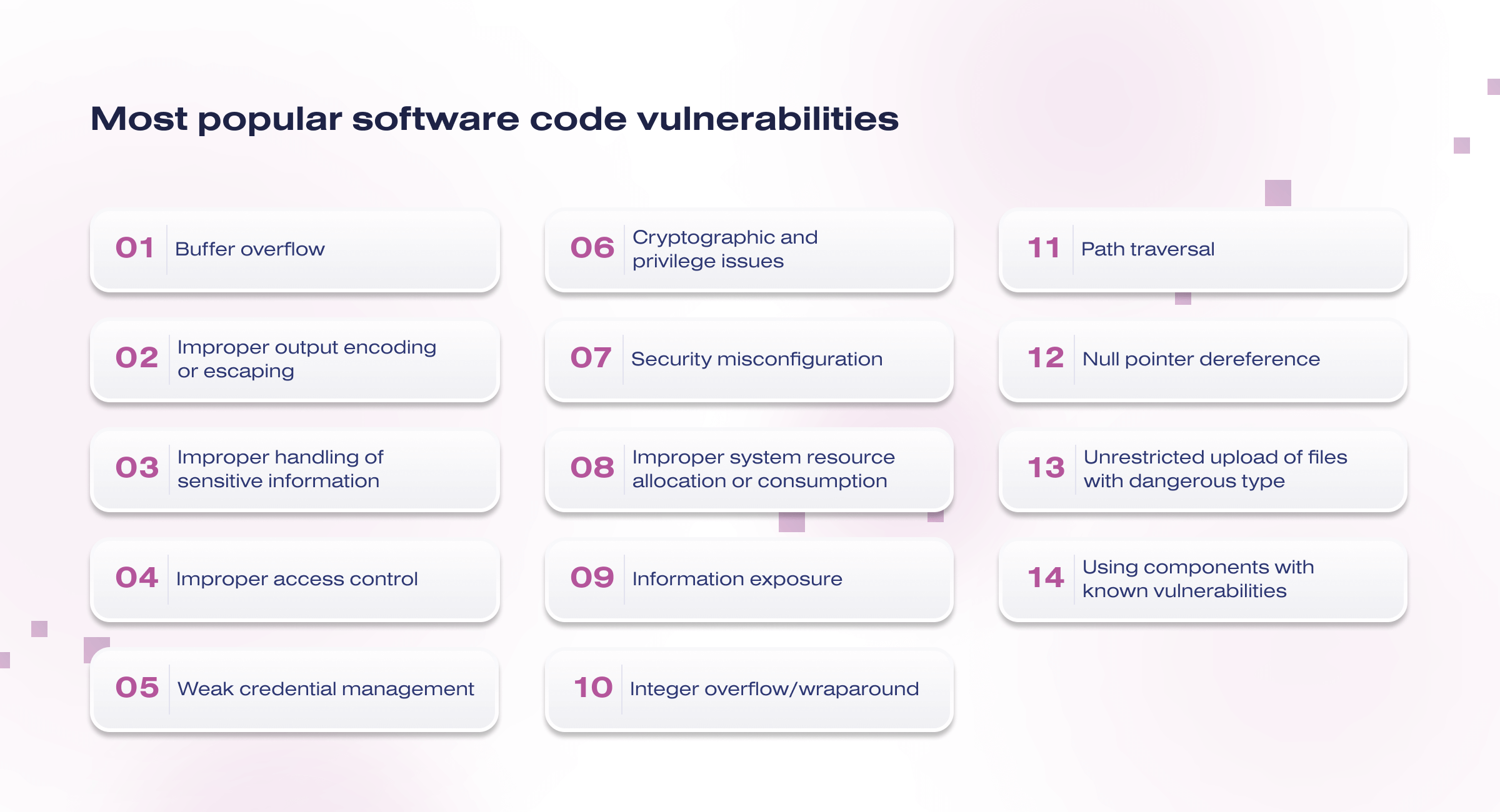
Here are the most popular software code vulnerabilities:
- Buffer overflow
- Improper output encoding or escaping
- Improper handling of sensitive information
- Improper access control
- Weak credential management
- Cryptographic and privilege issues
- Security misconfiguration
- Improper system resource allocation or consumption
- Information exposure
- Integer overflow/wraparound
- Path traversal
- Null pointer dereference
- Unrestricted upload of files with dangerous type
- Using components with known vulnerabilities
Essentially, it is a question of code compliance with the platform’s standards and programming language. The language itself also makes its own corrections in the situation with information security. Thus, C is the leader in the total reported open-source vulnerabilities, while C++, Ruby, and Python are considered among the safest. Still, it is not the language that matters but the skill of using it.
Types of software code review
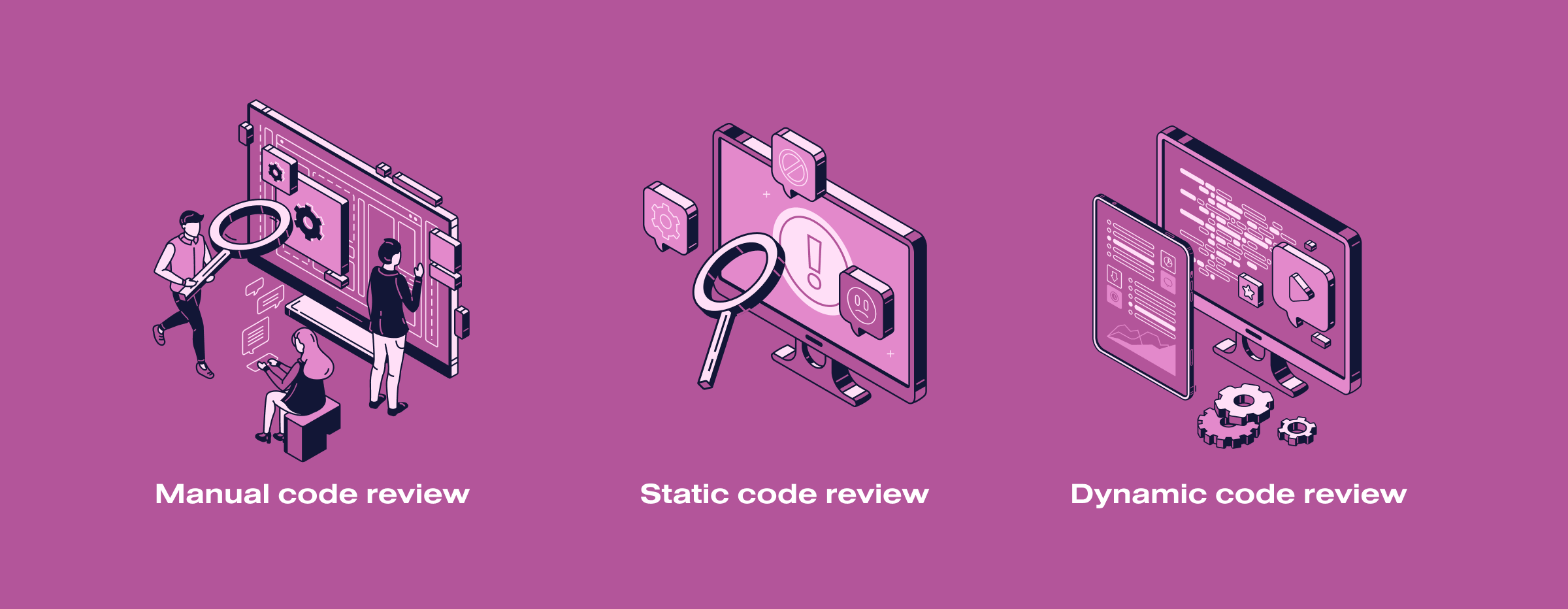
We outline 3 methods of software code review. Combining them makes it possible to regulate the depth and thoroughness of software security analysis along with effort, time, and cost. So, 3 methods of software code review:
- Manual code review. This is the most labor-intensive method available that requires involving highly qualified employees. It is even better to involve several independent groups of such experts to minimize the factor of subjective perception. Such code review will take a lot of time, but it will reveal masked flaws as well as architecture defects of the whole application and its separate subsystems.
- Static code review. The essence of this method is to check the program code by specialized utilities searching for potentially unsafe constructions. They often cannot detect complex flaws, but they can easily find typical vulnerabilities like SQL injections.
- Dynamic code review. It involves running code and examining the outcome. This method also implies automation and helps detect coding incorrectness and many vulnerabilities. Usually, dynamic software code audit is used as an additional method to clarify some aspects of application operation.
The best approach is combining all three methods. This guarantees a deep investigation of the code from different angles.
Core steps of the code audit process
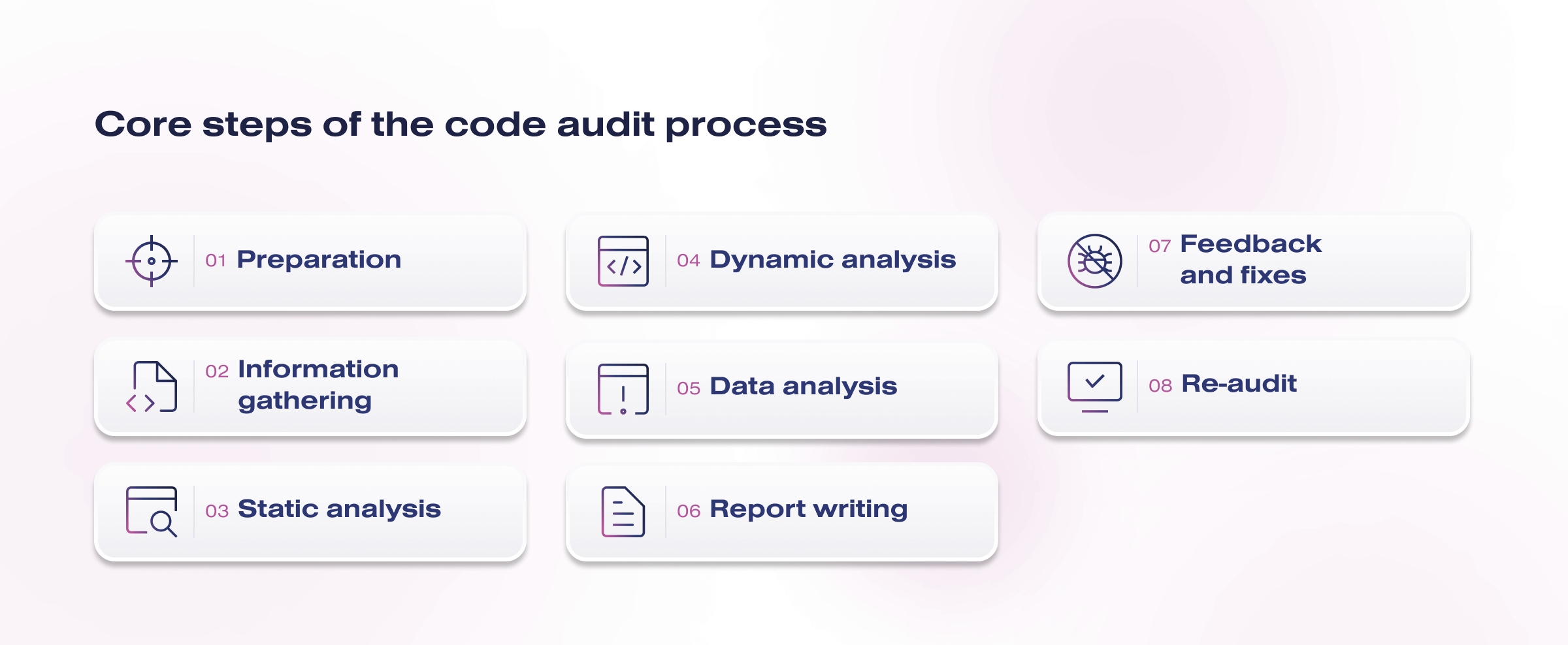
Here are the core steps that a code audit process typically involves:
- Preparation. In this step, the audit objectives, customer expectations, and the areas of code are defined. Security, performance, and other requirements may also be considered.
- Information gathering. Auditors collect and analyze available source code as well as related documentation. This may include manually and automatically retrieving code from repositories and analyzing comments, diagrams, and specifications.
- Static analysis. Auditors analyze source code without actually executing it. Specialized tools can be used to identify potential vulnerabilities, programming errors, and non-compliance with standards.
- Dynamic analysis. In this phase, code can be executed or simulated in a controlled environment. This allows you to identify bugs that may only appear during execution, such as memory leaks, performance issues, and other aspects unavailable in the static analysis phase.
- Data analysis. The static and dynamic analysis results are compared against expectations, standards, and best practices. Auditors identify potential problems and compile a list of recommendations for fixes.
- Report writing. A detailed report includes a description of the problems found, recommendations for fixing them and improving security, performance, and overall code quality.
- Feedback and fixes. Developers receive the report from the auditors and start fixing the identified issues. Feedback between auditors and developers can continue until all issues are fixed.
- Re-audit. After the changes are made, the corrected code is re-audited to ensure the problems have been fixed and no new ones have appeared.
Program code auditing is important to ensure a software product’s safety, reliability, and efficiency, as well as to improve development processes and educate developers on best programming practices.
What’s the price of a software code audit?
The price of a software code audit can vary widely depending on various factors such as the codebase’s size and complexity, the audit’s scope, the auditors’ expertise, the timeline for completion, and the goals of the audit. Here are some factors that can influence the cost of a software code audit:
- Codebase size and complexity. Larger and more complex codebases typically require more time and effort to audit, which can drive up the cost.
- Scope of the audit. The scope of the audit can vary. Some audits may focus on security vulnerabilities, while others might also include performance optimization, code quality assessment, and adherence to coding standards.
- Expertise of auditors. The experience and expertise of the auditors conducting the review will impact the cost. Highly skilled and specialized auditors may charge more for their services.
- Timeline. The timeline for completing the audit can affect the cost. Rush jobs or tight deadlines may come at a higher price.
- Post-audit support. Some auditing services may include post-audit support to help implement the recommended changes. This additional support can contribute to the overall cost.
Average hourly rates for code auditors:
- Junior auditor: $20 – $60 per hour
- Mid-level auditor: $60 – $100 per hour
- Senior auditor: $100 – $200+ per hour
Remember that a software code audit is an investment in the quality and security of your software, and it’s important to prioritize the expertise and reputation of the auditors alongside the cost.
Conclusion
Professionalism, attentiveness, and diligence are necessary for effective software code review. But we are convinced that the most important thing is to focus on the result. We mean creating crack-resistant software.
Only in one case, potential vulnerabilities do not turn into real losses – if you get rid of them in time. This means that software code auditing is also a guarantee of your peace of mind.